You can stay in touch with all things SCL through our news feed or attending one of our upcoming events. SCL includes some of the world’s most experienced researchers in their fields who enjoy sharing their perspectives on a wide variety of topics. Our faculty is world-renowned and our students are intellectually curious and our alumni can be found around the globe in leadership positions within a wide variety of fields.

SCL reaches out to students, educators, businesses and the logistics community in an effort to increase exposure and accessibility to supply chain & logistics expertise through a variety of educational programs, partnership opportunities and outreach activities.

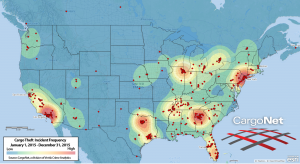
New ideas and new tools are born in the robust research environment supported by the Supply Chain & Logistics Institute. Solutions and improvements produced by researchers provide businesses with the high level of competitiveness that is critical to their success in the marketplace both at home and overseas.

Thousands of logistics and supply chain management professionals have advanced their knowledge—and their companies’ profitability—with the education they obtained through the courses and graduate degree programs offered through the Supply Chain & Logistics Institute and Stewart School of Industrial and Systems Engineering.